3 minutes
Uber Hack - Another Social Engineering Attack
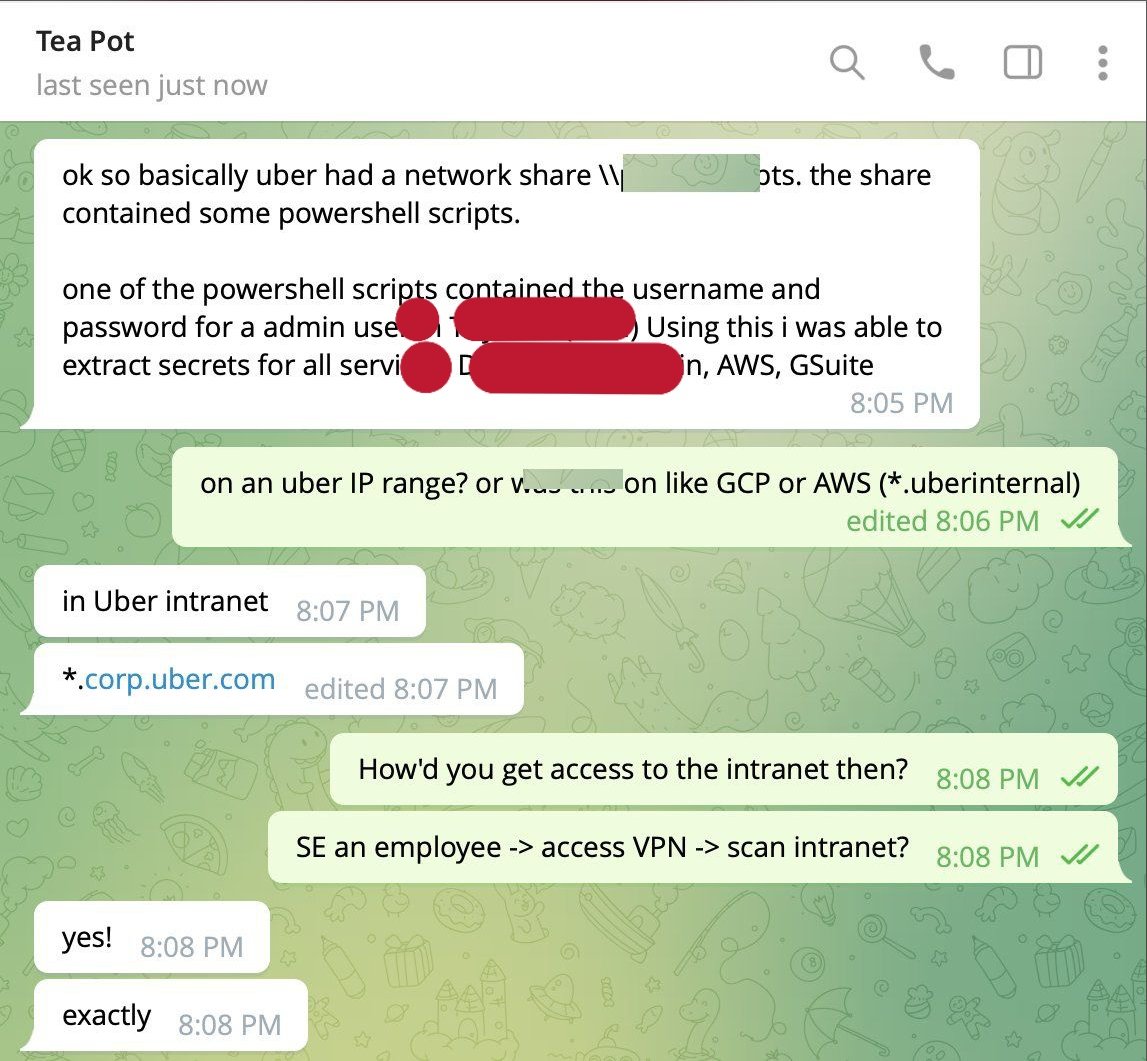
On September 15, reports came in that Uber was hacked and the hacker basically had the keys to the kingdom. The hacker was able to get access to Uber’s intranet after a social engineering attack that allowed the hacker to access vpn and subsequently Uber’s intranet. That was only the beginning though as the hacker was then able to pivot by looking through network shares and finding a powershell script with hardcoded admin credentials giving them admin access to multiple systems including AWS, GSuite, Slack, etc.
The alleged timeline that took place according to hacker from multiple reports is that they were able to social engineer an employee, spam the employee with MFA notifications until they accepted, connect to vpn, profit.
Screenshot of telegram exchange here
In my opinion, there were multiple security measures that could have been implemented to safeguard Uber’s data.
- Account lock for exessive MFA attempts - so that MFA wouldn’t have been spammed
- FIDO Authentication so that MFA wouldn’t have been so easily bypassed
- Certificate based authentication for VPN so that the hacker couldn’t connect to VPN
- No hardcoded admin credentials in scripts - This one was probably the biggest issue that someone hardcoded their admin credentials and they seemd to have admin access to everything.
- Least privilege/auditing - Why was there an account that allowed the hacker to get admin access to everything?
These were just some of my personal initial thoughts on the hack. I find it impressive how the hacker was able to pivot through and get admin access to eprivileged accounts even though it didn’t seem that sophisticated of an attack. It sounded like it was just a teenager who did it because they could. The hacker even created a slack account and posted in Uber’s slack channel stating that they hacked Uber and many folks thought it was just a joke. They were even able to get access to Uber’s hackerone vulnerability reports which means that they can easily exploit more vulnerabilities in uber’s infrastructure if those are still valid.
We talk about APTs all the time but sometimes even folks’ with less resources than APTs can still cause damage and hit high profile targets.
Best of luck to Uber’s blue team as they assess the damage. Uber has stated that they don’t see “any evidence” of the hacker accessing customers’ personal data. No evidence isn’t very reassuring though becuase that could mean they just haven’t located it yet.
Today, Uber has released a statement that they think that Lapsus$ was behind the hack.
sources: bleepingcomputer twitter twitter